What's going on at GCVE during the past 6 weeks?
GCVE.eu — Six Weeks of Progress: Standards, Implementations, and a Growing Ecosystem
The past six weeks have been an important milestone for the GCVE.eu initiative. What started as an experiment in decentralized vulnerability identification and coordination continues to evolve into a mature ecosystem supported by standards, implementations, and a rapidly growing community.
This post summarizes the latest developments across specifications, implementations, and community growth.
BCP-07 KEV Standard Published and Already Implemented
One of the most significant achievements is the official publication of BCP-07, defining the Known Exploited Vulnerabilities (KEV) standard within the GCVE ecosystem.
BCP-07 establishes a structured and interoperable way to share exploitation status information across GCVE Numbering Authorities (GNAs) and tooling ecosystems. The goal is simple but essential: provide reliable, machine-readable signals about vulnerabilities that are actively exploited in the wild.
Even more importantly:
✅ BCP-07 is already implemented in Vulnerability-Lookup.
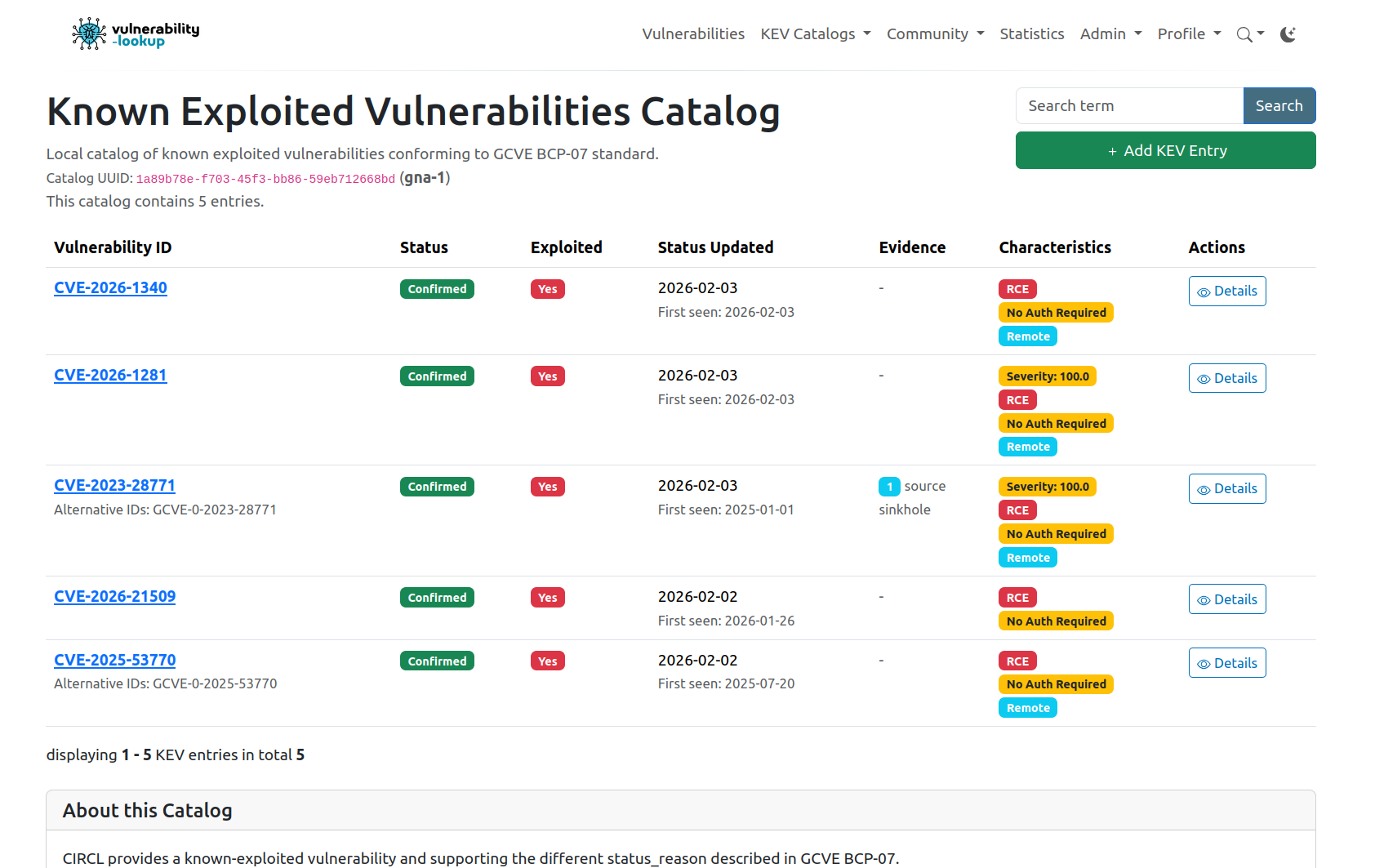
This immediate implementation demonstrates one of the core design principles behind GCVE: specifications are meant to be operational from day one, not theoretical documents waiting for adoption.
Extension: Evidence Calculation
Following the first real-world deployment, practical feedback quickly led to improvements. An extension to BCP-07 has been introduced to support confidence calculation, allowing:
- clearer justification of KEV status,
- improved transparency,
- better trust evaluation across GNAs,
- reproducible scoring and validation mechanisms.
This iterative evolution reflects the open governance model of GCVE specifications grow through implementation and operational experience.
First Draft of BCP-06: Evaluating GCVE Numbering Authorities
Another major step forward is the publication of the first draft of:
BCP-06 — Requirements and Evaluation Criteria for GCVE Numbering Authorities (GNAs)
BCP-06 answers an important question for decentralized vulnerability coordination:
How do we ensure quality and trust without centralization?
The document introduces:
- multiple GNA operational models,
- evaluation criteria for quality and reliability,
- governance expectations,
- transparency and accountability principles,
- guidance for assessing trustworthiness of numbering authorities.
Rather than enforcing a single rigid structure, BCP-06 recognizes diversity in operational realities while defining measurable quality indicators.
GCVE and the Cyber Resilience Act (CRA)
A new draft document explores how GCVE can support organizations facing upcoming regulatory requirements under the Cyber Resilience Act (CRA).
Draft available here:
The document outlines how GCVE may help with:
- vulnerability disclosure obligations,
- coordinated publication workflows,
- traceability of vulnerability handling,
- decentralized yet auditable processes,
- alignment with European regulatory expectations.
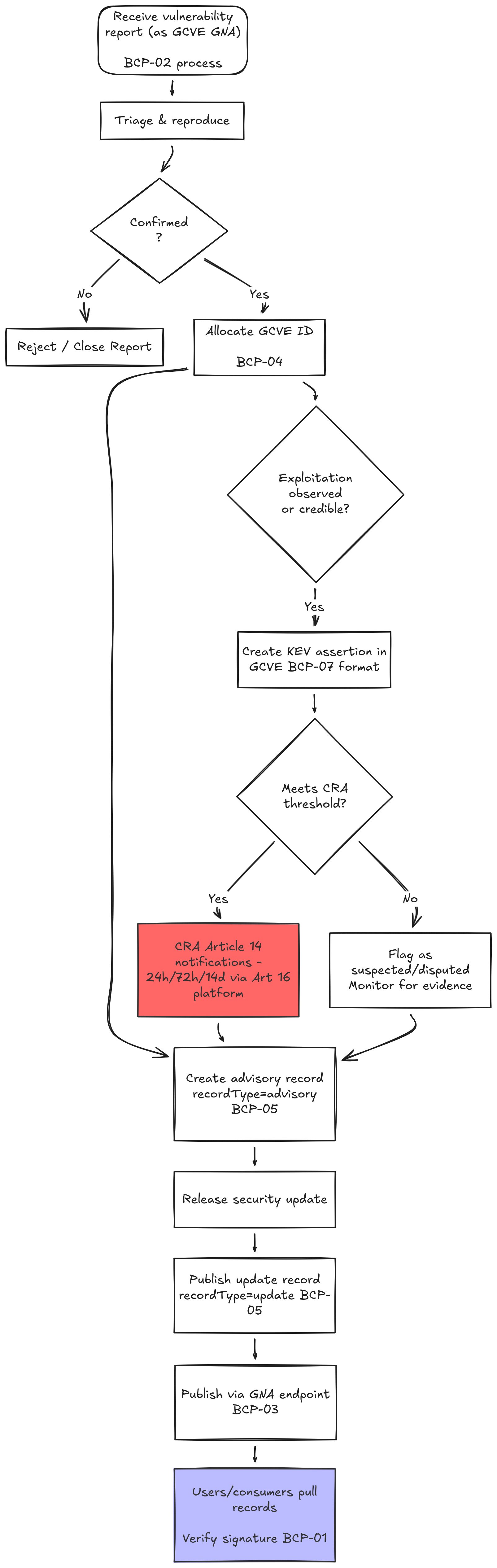
This work represents an important bridge between open-source infrastructure and regulatory compliance, showing how community-driven standards can reduce operational friction for vendors and maintainers.
New Ecosystem Page: Operational from Day One
To better support adopters, we introduced a new page listing all open-source software developed within the GCVE ecosystem.
The objective is practical:
Help users become operational immediately.
The page aggregates tools that enable:
- vulnerability publication,
- synchronization,
- lookup and enrichment,
- KEV consumption,
- GNA operations.
GCVE is not only defining standards, it is building a complete operational stack.
Community Growth and New Contributors
Beyond technical milestones, the most exciting development is the growth of the community around GCVE.
Over the past weeks we have seen:
- new contributors joining development and specification efforts,
- increased support from organizations and individuals,
- a growing number of GNA members,
- expanding adoption by early users and integrators.
This momentum confirms that decentralized vulnerability identification is not just a concept, it is becoming a shared effort supported by practitioners across ecosystems.
What This Means for GCVE
The last six weeks demonstrate a clear transition:
| Then | Now |
|---|---|
| Conceptual framework | Operational standards |
| Draft ideas | Implemented specifications |
| Early adopters | Growing ecosystem |
| Individual effort | Community-driven initiative |
GCVE is steadily moving toward a sustainable, decentralized model for vulnerability coordination — one that prioritizes openness, interoperability, and operational reality.
Thank You
None of this progress would be possible without the growing community supporting GCVE: contributors, GNAs, implementers, reviewers, and users providing feedback through real deployments.
The project is accelerating, and the ecosystem is expanding faster than ever.
If you are interested in participating — whether as a contributor, a GNA, or a user — now is the perfect time to get involved.
GCVE.eu continues to evolve collaboratively, openly, and operationally.